CloudSEK, an AI-driven Digital Risk Management Enterprise, has identified a 20% increase in cyber threats targeting the global education sector in the first quarter of 2022, as compared to the same period in 2021. Of the threats detected last year in Asia & Pacific, 58% of them were targeted at Indian educational institutions and online platforms. This includes attacks on major players like Byju’s, IIM Kozhikode, and Tamil Nadu’s Directorate of Technical Education.
CloudSEK’s investigation indicates that the majority of cyber incidents in 2021 targeted educational institutions in Asia & Pacific, followed by Europe, North America, South/ Latin America, and the Middle East. The growing global education and training market is a breeding ground for cybercriminals targeting entities and institutions in the sector. Remote learning, digitization of education, and prevalence of online learning platforms are key triggers that enlarged the attack surface.
The findings indicate that several cybercriminals are actively leaking databases, accesses, vulnerabilities/ exploits, and other information belonging to educational institutions, on cybercrime forums. Databases and accesses are the most commonly sought after data types. The databases leaked from educational institutions primarily contain:
- Personally Identifiable Information (PII) of students and their families, including name, date of birth, email address, phone number, and physical address.
- Website user records and credentials
- Examination results and scores
Increase in Dark Web Activity Related to Indian Education Sector
A threat actor advertised Citrix access to BYJU, an Indian multinational educational technology company, headquartered in Bangalore. In addition, another threat actor leaked BYJU’s databases. The data was purportedly exposed due to an unprotected SalesKen server that had been left unsecured, without a password, since 14 June 2021. The databases contained:
- PII and sensitive information related to students, parents, and instructors
- Conversation logs between parents and staff, including remarks about their children.
- Copies of emails with codes to reset user accounts and internal Salesken.ai data
Furthermore, a threat actor shared a post advertising access to the SMTP server and API credentials of allegedly the largest Indian ed tech platform.
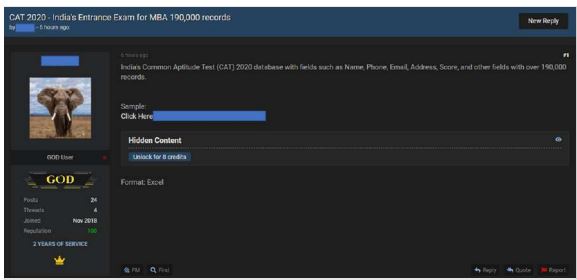
On 18 December 2021, a threat actor shared the database from Aakash Educational Services Limited (AESL), a leading test-prep company in India that provides test preparatory services for students preparing for Medical and Engineering entrance exams, School/Board exams, and competitive exams such as NTSE, KVPY, and Olympiads. The actor was found selling this data on multiple platforms.
A threat actor shared the PII from Tamil Nadu’s Directorate of Technical Education.
The two threat actors who go by the handles “babam” and “Kristina”, posted more data leaks and accesses than any other threat actor, find the full report [here]
Mitigation Measures
Given the size and impact of the education sector, it is critical for institutions, students, parents, teachers, and the government to ensure that the information gathered and stored is not leaked and exploited by cybercriminals. To ensure this, Educational institutions and related government entities need to:
- Create awareness among users regarding cyber-attacks, online scams, and phishing campaigns
- Enact strong password policies and enable multi-factor authentication (MFA)
- Update and patch software, systems, and networks on a regular basis
- Maintain multiple backups, both online and offline, in separate and secure locations
- Monitor logs for unusual traffic and activity to websites and other applications
- Block illegitimate IP addresses and deactivate port forwarding using network firewalls
- Perform real-time monitoring of the internet to identify and mitigate low-hanging threats, such as misconfigured apps, exposed data, and leaked accesses, that are leveraged by cybercriminals to carry out large scale attacks.
- Students, parents, faculty, and staff should:
- Avoid clicking on suspicious emails, messages, and links
- Not download or install unverified apps
- Use strong passwords and enable multi-factor authentication (MFA) across accounts